
This Azure vulnerability management guide explores how the cloud security landscape has evolved significantly in 2026, with Microsoft Defender for Cloud now serving as the central hub for identifying, prioritizing, and remediating risks across hybrid and multi-cloud environments. Powered by integrated Microsoft Defender Vulnerability Management, the platform combines agentless and agent-based scanning to deliver real-time insights into software vulnerabilities, misconfigurations, and exploit paths.
This guide provides a comprehensive overview of Azure vulnerability management in 2026 — including key tools, common vulnerabilities, best practices, and actionable steps for organizations to strengthen their cloud posture. As Azure adoption accelerates amid rising threats like AI-enhanced attacks and supply-chain compromises, proactive Azure vulnerability management is no longer optional; it’s essential for maintaining resilience and compliance.
Azure vulnerability management refers to the continuous process of discovering, assessing, prioritizing, and remediating security weaknesses in Azure workloads — spanning virtual machines (VMs), containers, serverless functions, databases, identity configurations, and more.
Under the shared responsibility model, Microsoft secures the underlying infrastructure, while customers own responsibility for patching guest OSes, securing configurations, and addressing application-layer risks. In 2026, this process leverages Microsoft Defender for Cloud as the unified platform, enriched with real-world exploitability data from sources like CISA KEV, MSRC, and reachability analysis.
Key advancements include:
Effective management reduces breach windows by focusing remediation on exploitable issues first, rather than overwhelming teams with high-volume CVEs.
In 2026, Microsoft has further unified vulnerability insights under Exposure Management in the Defender portal, allowing security teams to view and prioritize risks with runtime context, AI-assisted remediation suggestions, and traceability from code repositories (GitHub/Azure DevOps) to deployed workloads. This reduces alert fatigue by focusing on truly exploitable issues rather than theoretical CVEs.
Microsoft provides native, integrated capabilities that form the backbone of Azure vulnerability management in Azure environments.
Transitioning to the built-in Defender solution (from legacy Qualys/Tenable) is recommended for streamlined operations and better exploitability context.
Microsoft continues to evolve Defender for Cloud with:
These updates streamline operations for hybrid/multi-cloud setups, with automatic recommendations and Azure Policy enforcement reducing manual overhead.
Despite robust tools, organizations continue to face recurring issues that expose environments to exploitation. Emerging 2026 threats include AI-enhanced exploit generation and sophisticated supply-chain attacks targeting open-source dependencies — making reachability analysis essential to filter noise and prioritize fixes that attackers can actually chain.
Prioritizing via exploit paths (e.g., in Defender portal’s Exposure Management) helps teams focus on critical risks over volume.
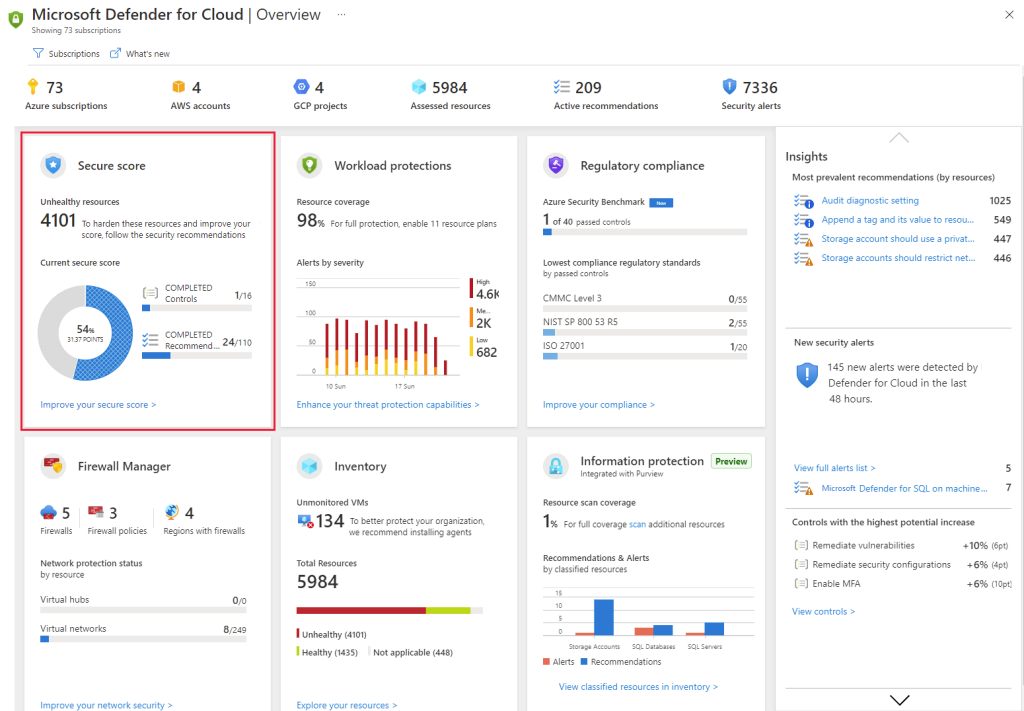
Management scan results showing prioritized findings in Microsoft Defender for Cloud
Adopt these steps to build a mature program aligned with 2026 threats.
Consistency across hybrid environments — including Arc-onboarded machines — ensures no blind spots.
To strengthen Azure vulnerability management immediately:
Implementing these reduces mean time to remediate and aligns with evolving compliance frameworks.
Azure vulnerability management in 2026 reflects a shift toward automated, exploit-focused, and integrated security. With features like reachability SCA (Endor Labs native), expanded container coverage (external registries, Chainguard/Wolfi), serverless posture extensions, and tighter Defender portal unification (including Exposure Management), Microsoft continues to reduce manual overhead while elevating prioritization accuracy.
Yet the threat landscape remains dynamic — AI-driven attacks, sophisticated ransomware, and nation-state operations demand ongoing vigilance. As 2026 progresses, expect deeper AI integration for predictive vulnerability forecasting, expanded multicloud parity (AWS/GCP connectors), and automated attestation for compliance-heavy industries. Organizations that treat vulnerability management as a continuous, proactive program — rather than a checklist — will maintain stronger resilience against emerging risks.

This Azure vulnerability management guide explores how the cloud security landscape has evolved significantly in 2026, with Microsoft Defender for Cloud now serving as the central hub for identifying, prioritizing, and remediating risks across hybrid and multi-cloud environments. Powered by integrated Microsoft Defender Vulnerability Management, the platform combines agentless and agent-based scanning to deliver real-time insights into software vulnerabilities, misconfigurations, and exploit paths.
This guide provides a comprehensive overview of Azure vulnerability management in 2026 — including key tools, common vulnerabilities, best practices, and actionable steps for organizations to strengthen their cloud posture. As Azure adoption accelerates amid rising threats like AI-enhanced attacks and supply-chain compromises, proactive Azure vulnerability management is no longer optional; it’s essential for maintaining resilience and compliance.
Azure vulnerability management refers to the continuous process of discovering, assessing, prioritizing, and remediating security weaknesses in Azure workloads — spanning virtual machines (VMs), containers, serverless functions, databases, identity configurations, and more.
Under the shared responsibility model, Microsoft secures the underlying infrastructure, while customers own responsibility for patching guest OSes, securing configurations, and addressing application-layer risks. In 2026, this process leverages Microsoft Defender for Cloud as the unified platform, enriched with real-world exploitability data from sources like CISA KEV, MSRC, and reachability analysis.
Key advancements include:
Effective management reduces breach windows by focusing remediation on exploitable issues first, rather than overwhelming teams with high-volume CVEs.
In 2026, Microsoft has further unified vulnerability insights under Exposure Management in the Defender portal, allowing security teams to view and prioritize risks with runtime context, AI-assisted remediation suggestions, and traceability from code repositories (GitHub/Azure DevOps) to deployed workloads. This reduces alert fatigue by focusing on truly exploitable issues rather than theoretical CVEs.
Microsoft provides native, integrated capabilities that form the backbone of Azure vulnerability management in Azure environments.
Transitioning to the built-in Defender solution (from legacy Qualys/Tenable) is recommended for streamlined operations and better exploitability context.
Microsoft continues to evolve Defender for Cloud with:
These updates streamline operations for hybrid/multi-cloud setups, with automatic recommendations and Azure Policy enforcement reducing manual overhead.
Despite robust tools, organizations continue to face recurring issues that expose environments to exploitation. Emerging 2026 threats include AI-enhanced exploit generation and sophisticated supply-chain attacks targeting open-source dependencies — making reachability analysis essential to filter noise and prioritize fixes that attackers can actually chain.
Prioritizing via exploit paths (e.g., in Defender portal’s Exposure Management) helps teams focus on critical risks over volume.

Management scan results showing prioritized findings in Microsoft Defender for Cloud
Adopt these steps to build a mature program aligned with 2026 threats.
Consistency across hybrid environments — including Arc-onboarded machines — ensures no blind spots.
To strengthen Azure vulnerability management immediately:
Implementing these reduces mean time to remediate and aligns with evolving compliance frameworks.
Azure vulnerability management in 2026 reflects a shift toward automated, exploit-focused, and integrated security. With features like reachability SCA (Endor Labs native), expanded container coverage (external registries, Chainguard/Wolfi), serverless posture extensions, and tighter Defender portal unification (including Exposure Management), Microsoft continues to reduce manual overhead while elevating prioritization accuracy.
Yet the threat landscape remains dynamic — AI-driven attacks, sophisticated ransomware, and nation-state operations demand ongoing vigilance. As 2026 progresses, expect deeper AI integration for predictive vulnerability forecasting, expanded multicloud parity (AWS/GCP connectors), and automated attestation for compliance-heavy industries. Organizations that treat vulnerability management as a continuous, proactive program — rather than a checklist — will maintain stronger resilience against emerging risks.